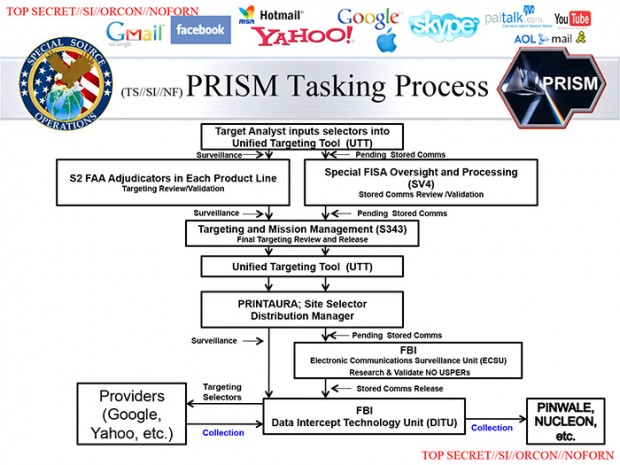
Thanks to information provided by Edward Snowden, the now fugitive whistleblower still at large, last month information about the US government’s top secret surveillance program PRISM emerged. According to the information Snowden provided, the NSA and FBI have direct access to the servers to major tech companies (and thus direct access to user data)… an allegation the tech companies denied. It still isn’t entirely clear what is true and what is not but the Washington Post has just published new slides about PRISM.
According to the newly published slide, with PRISM the US government employs equipment on the property of companies such as Microsoft or Yahoo to retrieve information as desired on a real-time basis, which is then forwarded to a relevant security agency such as the NSA. Said equipment used for the operations is managed by the FBI who is then responsible for forwarding the information to the NSA or CIA.
The Washington Post also says that the system lets the NSA to “receive live notifications when a target logs on or sends and email.” It also lets the spy agency to “monitor a voice, text or voice chat as it happens.” However, it should be mentioned that it is not clear if the NSA is conducting this real-time monitoring on a general basis (i.e. monitoring everyone) or just monitoring specific targets. If I were to guess, I would say the latter but the truth is we don’t really know.
Internet companies mentioned in the slides include Microsoft, Apple, Facebook, AOL, Skype, Yahoo, and Google, most all of whom have already denied their participation in the program. It’s now up to us about whom to believe — especially considering there are conflicting reports as to what is the real truth.
More information about the new slides can be found in the via link below.
[via The Washington Post]

 Email article
Email article