What’s that program you have running that’s accessing the internet? You don’t know? Find out using a simple command prompt command. It’s important to know what your programs are doing at any one time. You should have full control over what does and doesn’t use your connection, whether you’re at home or running on an O2 UK 3G dongle. This is a simple and effective process that allows for the monitoring of your system. Just follow the instructions and you’ll remain well-informed.
What’s that program you have running that’s accessing the internet? You don’t know? Find out using a simple command prompt command. It’s important to know what your programs are doing at any one time. You should have full control over what does and doesn’t use your connection, whether you’re at home or running on an O2 UK 3G dongle. This is a simple and effective process that allows for the monitoring of your system. Just follow the instructions and you’ll remain well-informed.
 more–>
more–>
Step One: Windows XP
Open up the Run box by pressing the Windows key and R at the same time.
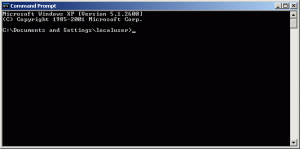
Put in CMD and press OK. The command prompt window will open up:
Step One: Windows Vista/Windows 7
Open the Start menu (![]() ) and type in CMD:
) and type in CMD:
Right click on it and select Run as Administrator:
Step Two
In your open Command Prompt window, enter the following:
netstat -b 5 > activity.txt
and hit enter. (Note: to paste something into Command Prompt, you’ll need to right click and click paste.)
If you forgot to run the prompt as an administrator (like I did in the screenshots above), just redo step one You can tell when it’s running as administrator because instead of saying C:\Users\Username it says C:\Windows\system32.
If you’ve pasted the code right, a blinking cursor will… blink.
After a few minutes, press Ctrl+C. That’ll stop the command.
Now type in activity.txt to open the log:
When you press Enter, your default text editor-probably Notepad-will open:
Now, scroll through the lists. You’ll see that it’s mostly your browser-but some times, there are programs like Google Talk’s webcam program installed that call home even when you aren’t using them.
Now that you’ve found any and all culprits that are programs accessing the internet (with and without your knowledge), you can either close them from the Task Manager or even uninstall them.
UPDATE:
I’ve made a short (1 minute) video on doing this.
UPDATE 2: Clarified the Windows XP instructions.
[[Via Lifehacker via Cogizio]]
This article was written by Locutus on his tech blog Cogizio. You can read the original article here.
![]() photo credit: balloon tiers
photo credit: balloon tiers

 Email article
Email article