You know that Internet Explorer vulnerability affecting Internet Explorer 7/8/9 on Windows XP/Vista/Win7 dotTech recently posted about? Yeah, well, it looks like Microsoft is on the ball with this one; they have just issued an easy-to-apply ‘Fix it’ to patch the vulnerability. According to Microsoft, “applying the Fix it solution, ‘Prevent Memory Corruption via ExecCommand in Internet Explorer,’ prevents the exploitation of [the] issue.” Anyone with Internet Explorer 6/7/8/9 on their computer is highly recommended to apply the fix — it takes literally less than 30 seconds and doesn’t even require you to reboot your computer.
You know that Internet Explorer vulnerability affecting Internet Explorer 7/8/9 on Windows XP/Vista/Win7 dotTech recently posted about? Yeah, well, it looks like Microsoft is on the ball with this one; they have just issued an easy-to-apply ‘Fix it’ to patch the vulnerability. According to Microsoft, “applying the Fix it solution, ‘Prevent Memory Corruption via ExecCommand in Internet Explorer,’ prevents the exploitation of [the] issue.” Anyone with Internet Explorer 6/7/8/9 on their computer is highly recommended to apply the fix — it takes literally less than 30 seconds and doesn’t even require you to reboot your computer.
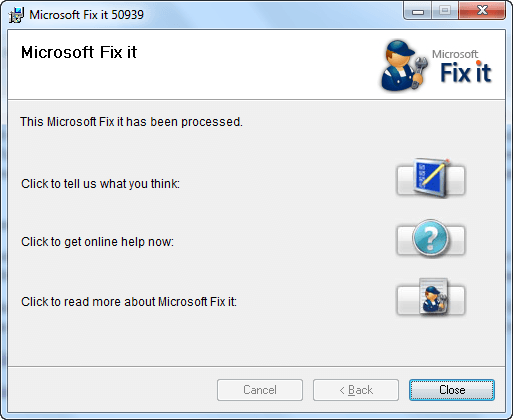
At the end of this article you will find the relevant links you need to use the Fix it. To apply the Fix it, simply click on the “Enable Fix it (direct download)” link you see below to download the fix. Once the download is finished, run the EXE file, accept “Software License Terms”, then wait while the Fix it does its thing (a system restore point will be created before the fix it applied; if you are on Windows Vista or higher, you will be prompted by UAC). You know the Fix it has been successfully applied when you get the following message:
Overall it should take you less than 30 seconds from start to finish. If it takes longer then something is probably wrong.
You can grab the Fix it from the links below.
Enable Fix it (direct download) | Disable Fix it (direct download)
Fix it homepage | Microsoft security bulletin
[via TheNextWeb]

 Email article
Email article