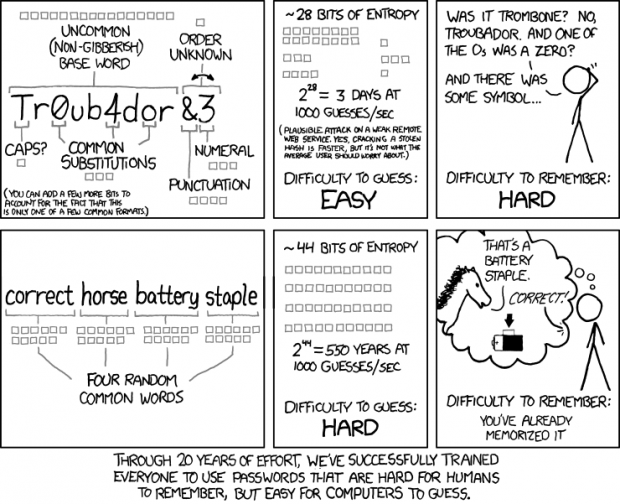
What makes a password stronger, complexity or length? Should you use a short password that mixes special characters with numbers and the alphabet or should you have long, simple passwords? Based on my knowledge, a longer, simple password that is made up of random words or phrases is more secure than a shorter password consisting of special characters and the like. Apparently the artist from xkcd agrees with me:
[via xkcd]

 Email article
Email article