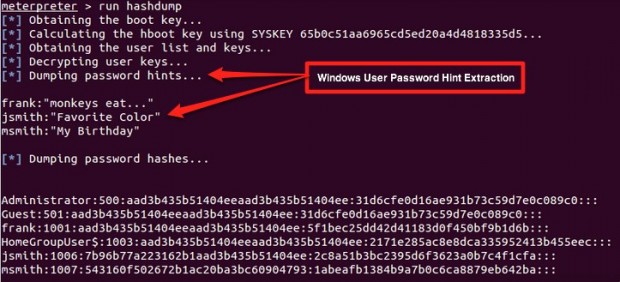
Do you have a password set to protect your Windows account? If you do, then more likely than not you setup a reminder hint to help you remember the password in case you ever forget. Microsoft claims this password hint is only accessible to someone physically accessing a Windows PC, meaning to see the hint you would have to be in front of the computer you are trying to hack. According to Jonathan Claudius, a security researcher at Trustwave’s SpiderLabs, there is an exploit hackers can use to remotely access the password reminder hints users set for Windows passwords.
The exploit revolves around Microsoft’s decision to store the password hint in the Windows registry in a cryptographically weak manner. According to Claudius, password hints are stored in a humanly unreadable form but are easily decoded using a simple decode algorithm. Anyone that has access to a password hint hash can decode the hash to reveal the password hint, which in turn would aid hackers (whitehat and blackhat) in guessing the password that protects the Windows PC.
It should be noted that breaking or bypassing a Windows user account password is an easy task if you have physical access to the machine, using tools such as Offline NT Password & Registry Editor or Ophcrack. What makes this vulnerability particularly worrisome is anyone, through the use of various different hacking techniques, can remotely intercept the password hint hash and decode it. Note the emphasis on “remotely” — the ability to figure out the password hint without ever physically touching the computer in question.
Claudius confirms this vulnerability exists in Windows 7 and Windows 8; both these operating systems store the password hint hash at the HKLM\SAM\SAM\Domains\Account\Users\<userkey>\UserPasswordHint registry location. While he doesn’t provide details, Claudius acknowledges that this vulnerability exists in Windows XP, too, although the password hint hashes are stored in a different location in the registry. My guess is since it exists in Windows XP and Windows 7, Windows Vista is probably also affected.
Now some people may argue why is this a big deal. Remotely decoding password hints? So what! They aren’t getting access to the passwords. Calm down, bro. This vulnerability may not be as significant as a remote password hack but it is still very important because it opens up an attack vector that was previously unknown. Microsoft needs to patch this… the sooner, the better.
[via ArsTechnica]

 Email article
Email article