Perhaps you’ve heard of Helen of Troy, the most beautiful woman in the world, the cause of the Trojan War in ancient Greece. If you’re familiar with the story, you probably know that the city of Troy put up a good fight until they were defeated by an enemy that had sneaked behind their defenses and ambushed them suddenly. The attacking soldiers build a giant hollow horse statue and filled it with warriors. They then presented it to Troy as a gift of peace. After the Trojans brought the horse into the city, the soldiers poured out of it at night and ransacked the city from the inside, opening the gates to allow their fellows inside the defenses.
Computer viruses called “Trojans” do the same thing. They sneak into your computer through some subtle method and destroy it from the inside out. There are several types of Trojan viruses. Read on to learn more.
ALSO READ: 12 ways how to know if your computer has a virus [Guide]
BEFORE WE BEGIN
If you want to delete a Trojan virus you have to determine the type of Trojan first. Here are some of the most common.
- Destroy: The most common type is to delete files such as DLL, EXE, INI. It acts like bomb with a timer that activated by hackers.
- Remote Control: This type of Trojan might inject a client app into your computer that is under the full control of the hacker. All your files can be opened and copied. Your whole computer is at the mercy of the hacker. He or she can do all kinds of operations on your computer such as turning off and on the webcam.
- Send Password: This type of Trojan automatically searches for useful passwords and sends them to a designated hacker’s e-mail address.
- Recording Keyboard: It is as simple as it sounds. It records all your keyboard activities.
- DOS attack: This type of Trojan is used to continuously attack the computers that are connected with the one that the Trojan virus is hidden on. This causes a traffic jam on the network or internet connection.
- FTP: This type waits for users to connect to a network. The Trojan virus infecting your computer automatically activates as soon as you open a web page or get on an FTP server.
- Program killer: The ones above can be detected and deleted by antivirus software. This one’s task is turning off antivirus software on the infected computer.
Trojan viruses have evolved into more and more advanced types that cannot be detected easily by many antivirus programs.
CHECKING YOUR COMPUTER FOR TROJANS
If your computer begins running slowly and you suspect a hidden Trojan file that your antivirus software has not found, there are some methods you can use to try to find the file.
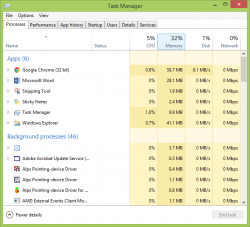
- Check your “Task Manager”. Press “Ctrl+Shift+Esc” and turn the “Task Manager” on. Find the irregular processes (In order to recognize irregular processes, you need to regularly check your task manager so that you can familiarize yourself with normal processes. These will vary from person to person and computer to computer, depending on the software you use. Therefore, in order to protect your computer, you need to make yourself familiar with what processes usually run on your Task Manager. Then, when you see an unfamiliar process, you can be almost certain it is a Trojan.). If you see an abnormal process, do not try to terminate it right away because if it is a Trojan, it probably will not allow you to close it anyway. Instead, check the status of the suspected Trojan; if your CPU or memory usage is as high as 100%, then you have most likely found the Trojan file.
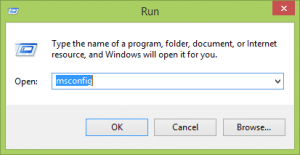
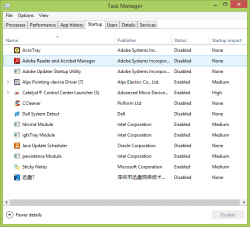
- Run your registry and check those apps which start with the system. Press “Win + R” and turn on the command box and type “msconfig”. Check if there are irregular startups in the startup selection. (For Windows 8 users, you can directly turn on “Task Manager” and locate the “Startup” section) Some viruses might auto start with the windows system and infect your computer.
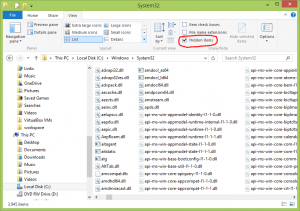
- Unmark hidden files and folders in your computer and check the system folder “system32”. If it is empty after you double clicked on it, you can confirm that your computer is infected.
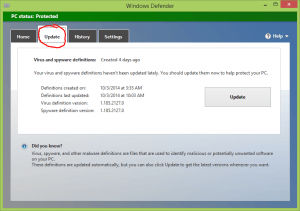
- If your antivirus software stops updating its database and manual updates do not take effect you can safely assume that your computer is infected.
WHAT NEXT?
Once you have detected some abnormal file or process on your computer, your next step is to remove it. See one of our articles covering a variety of antivirus or cleaning software for instructions on how to remove the discovered Trojan file.

 Email article
Email article