I’ve known malware exists on computers for almost as long as I can remember. Since the birth of smartphones back in 2007 with the iPhone 3G, we haven’t had to worry much about malware or viruses from a smartphone standpoint. So far, we have not seen a virus on smartphone replicate like it can on a computer, so technically, we haven’t seen an Android or iOS virus. Malware is a term we know, like a virus which is malicious software. Malware we know does exist on Android and iOS platforms and the most common way to come across malware is with apps.
I’ve known malware exists on computers for almost as long as I can remember. Since the birth of smartphones back in 2007 with the iPhone 3G, we haven’t had to worry much about malware or viruses from a smartphone standpoint. So far, we have not seen a virus on smartphone replicate like it can on a computer, so technically, we haven’t seen an Android or iOS virus. Malware is a term we know, like a virus which is malicious software. Malware we know does exist on Android and iOS platforms and the most common way to come across malware is with apps.
Android, Apple and Windows have security measures in place to protect their respective app stores to keep them malware free. Every now and then that security is breached, just like a few days back when the XcodeGhost malware was discovered.
XcodeGhost is malware first found by Palo Alto Networks when they discovered the code infecting several apps. Since the news broke, many sites have reported on the list of known apps that are infected; however, we don’t necessarily know all of the apps that are infected yet. According to reports, it isn’t possible for the XcodeGhost team to have installed the malware on the applications themselves. It happened when the app developers mistakenly installed the malware themselves by using some Xcode work during their developments.
There is a way you can detect XcodeGhost malware in iOS apps thanks to a new tool that’s made by the Pangu jailbreak team. We all know the Pangu team as students from Stefan Esser’s jailbreaking classes. Many people — include Stefan Esser himself — doubted Pangu’s integrity and ability when the Pangu jailbreaking tool was originally released. Those views from Esser, as well as the general public, might be about to change after checking out this latest tool that let’s us check out how to detect XcodeGhost malware in iOS apps.
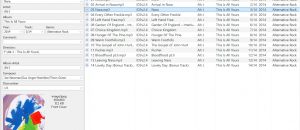
The list of infected apps as identified by Palo Alto:
- Didi Chuxing (developed by Uber’s biggest rival in China Didi Kuaidi)
- Angry Birds 2 (Chinese version)
- NetEase
- Micro Channel
- IFlyTek input
- Railway 12306 (the only official app used for buying train tickets in China.
- The Kitchen
- Card Safe
- CITIC Bank move card space
- China Unicom Mobile Office
- High German map
- Jane book
- Eyes Wide
- Lifesmart
- Mara Mara
- Medicine to force
- Himalayan
- Pocket billing
- Flush
- Quick asked the doctor
- Lazy weekend
- Microblogging camera
- Watercress reading
- CamScanner
- CamCard (a very popular business card reader.)
- SegmentFault
- Stocks open class
- Hot stock market
- Three new board
- The driver drops
- OPlayer
- Telephone attribution assistant
- Marital bed
- Poor tour
- I called MT
- I called MT 2
- Freedom Battle
If you are running any of the aforementioned apps from the list, or you have a number of other apps you would like to check are safe, XcodeGhost tool page on the Pangu website.
1. Visit the link from your mobile browsers — Google Chrome or Safari.
2. Tap your finger over the blue button with Chinese writing. (The Pangu team is Chinese)
3. Wait a few moments for the tool to take over your device and tap the ‘Install’ button when it comes up on the display.
4. Now you must navigate to Settings > General > Profiles and then highlight “Shenzhen Avaintel Technology”, and tap on the “Trust” option on the display before the tool will work.
5. Head out of there and back to the homescreen.
6. Navigate to your apps and launch the Pangu app.
Tap over the blue button with Chinese writing and you’re done.

 Email article
Email article