We’ve all heard the stories about malware and Android. Many believe the claims to be false, especially considering most malware has to be actively installed by the user before it can cause any damage. The biggest problem with malware is that it can be embedded in alternate software, and users don’t even know they’re installing it.
Apparently security researchers have discovered a group of malware specifically designed for Android phones, that’s been downloaded as much as 9 million times from the Google Play Store.
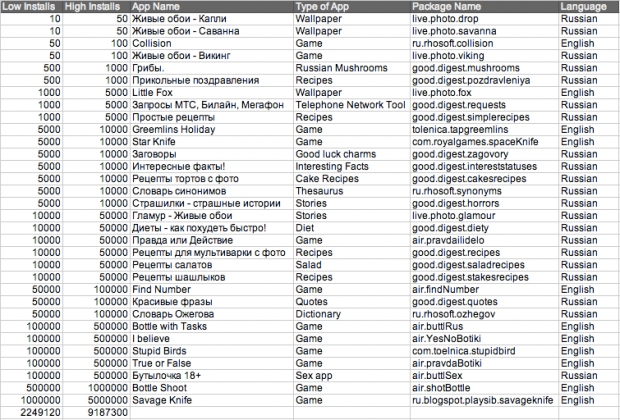
This particular malware instance has been given the name ‘Badnews,’ and it’s well deserved too. It’s found its way into at least 32 different applications offered by four developer accounts:
All of this was revealed by the Lookout Mobile Security Android app developer on a blog post yesterday.
Infected phones connect to a master server and send out sensitive information like the phone number of the device, the phone’s serial number and even the IMEI number (International Mobile Station Equipment Identity). In some cases, the control servers make the connected devices prompt installation of an app called AlphaSMS. The SMS app is essentially a Trojan that sends text messages to various services, thus adding charges to the users account.
The way the app developers were able to get infected software into the Google Play catalog is imaginative. They actually uploaded clean applications first, and then after they had already been submitted in the Play store they released an update which activated the malicious activities.
According to Google Play statistics the related apps have been download anywhere from 2 million to 9 million times. Although, those numbers may not accurately reflect which versions were carrying out malicious activities.
In an interview with Ars Technica, Marc Rogers the Principal Security Researcher for Lookout made the following statement:
“You can’t even say Google was at fault in this because Google very clearly scrutinized all these apps when they want in, but these guys were cunning enough to sit there for a couple of months doing absolutely nothing and then they pushed out the malware.”
It’s not quite clear how the Badnews system was adopted by many of the apps, which varied from things like games, dictionaries, and more. Obviously some were created by those who also generated the malware code. Rogers says that some developers may have been unaware the malicious matter was being added into their app.
“This is a wakeup call for us in the industry to say: ‘Bad guys are smart as well and they’ll take a look at the security models we put in place and they’ll find weaknesses in them. That’s exactly what they’ve done here.”
It’s sad to see Android users as the main target for a lot of these malicious apps, but then again it just takes a little discretion to avoid them. You just need to pay attention to what permissions apps are asking for when you install them.
[via Ars Technica]

 Email article
Email article