Did you think the Stuxnet and Flame were the end of geographically targeted malware attacks? Yeah, you wish. A new malware has been detected roaming in the Middle East, targeting ‘sensitive’ organizations and stealing e-mails, passwords, files, and nearby conversations.
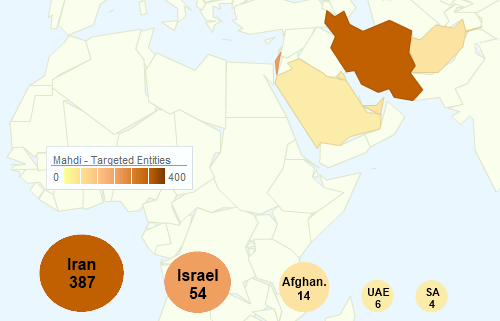
Dubbed ‘Mahdi’ by researchers at Kaspersky Lab and Seculert due to the strings and handles used by the attackers, the malware has hit the Middle East with Iran and Israel being its primary targets:
Originally Mahdi was thought to be connected with Flame. However, after further analysis it is quite clear the level of sophistication Flame has is not present in Mahdi. Unlike Flame which uses advanced coding and attack vectors, Mahdi contains amateur coding and relies on social engineering to infect computers. Mahdi primarily spreads through e-mail attachments; users are sent e-mails about various topics and are encouraged to click on the files attached. Attached files appear to be innocent files, such as images, but in fact contain Mahdi’s payload. Anyone that clicks on the attachment is then infected.
Active since December 2011, Mahdi has infected over 800 computers worldwide. According to Seculert, Mahdi primarily targeted (targets) critical infrastructure companies, financial services, and government embassies in Iran, Israel, and other countries in the Middle East.
Flame has been confirmed to be a US and Israel sponsored malware. If similarities between Mahdi and Flame were found, then it could have been said Mahdi is another state-sponsored attack. However, as mentioned above, there are clear differences between Flame and Mahdi making it unlikely to have originated from US or Israel. So, then, where did Mahdi come from? There are a few possibilities.
Firstly, it should be mentioned ‘Mahdi’ is a reference to a person in Islamic literature. As such, Mahdi could very well have originated in the Middle East. But where in the Middle East? Mahdi could be a state-sponsored attack but sponsored by a state that doesn’t have advanced NSA-like resources, hence the amateur coding. Alternatively, Mahdi could be a product of criminal organizations or other non-state actors who are interested in spying on sensitive locations. On the other hand, Mahdi could still be sponsored by US or Israel (or other countries outside the Middle East) with the references to Islamic literature, noob coding, and low-key attack vectors being used as a guise to through people off the proper trail.
Whatever the case may be, it is clear cyber espionage is alive and well in the Middle East. Road trip, anyone?
[via ArsTechnica | Image credit: Seculert Blog]

 Email article
Email article