Between the likes of Flame, Stuxnet, and Mahdi I’m sure most people have had their fair share of state-sponsored cyber attacks. As much as we wish they would go away, they won’t. In fact, they are likely to increase as geopolitical tensions take center stage. Indeed another state-sponsored malware has been discovered and once again it is targeting the Middle East.
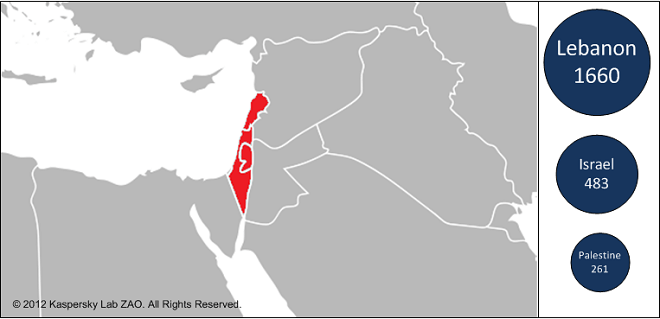
Dubbed ‘Gauss’ by researchers at Kaspersky Labs due to a component of the malware being named Gauss by its developer, this new malware is said to share traits with the likes of Flame, Stuxnet, and Duqo. Gauss is “highly modular” and shares a “fair deal of code” with Flame, leading researchers to believe they are both connected in some way, most likely having the same developers. And like recent state-sponsored attacks, Gauss’ primary targets are in the Middle East albeit Iran gets a reprieve on this one with Lebanon, Israel, and Palestine being the most heavily hit:
According to Kaspersky, the primary purposes of Gauss appears to be information gathering as opposed to digital disruption or financial theft:
- Intercept browser cookies and passwords.
- Harvest and send system configuration data to attackers.
- Infect USB sticks with a data stealing module.
- List the content of the system drives and folders
- Steal credentials for various banking systems in the Middle East.
- Hijack account information for social network, email and IM accounts.
Probably the most eye-popping target of Gauss are the financial institutions it targets. Gauss is said to have the ability to monitor and steal info from users of PayPal, Citibank, and several Lebanese banks. According to Kaspersky, “this is actually the first time we’ve observed a nation-state cyber-espionage campaign with a banking Trojan component”. Kaspersky is also quick to note it doesn’t appear as if the banking component of Gauss is intended for financial gain.
Interestingly enough, Gauss has a ‘mystery payload’ in the form of encrypted files. Kaspersky has not been able to decrypt the payload so no one is sure what it does or under what conditions it activates. Kaspersky also notes Gauss may have other ‘plugins’ not yet discovered that offer other functionality to the malware. Some experts suggest the encryption is intended to prevent people from accessing the code for ‘copycat’ malware.
Gauss has infected 2,500 systems connected to Kaspersky’s cloud network with the possibility of infecting thousands yet undiscovered machines. The command-and-control servers for Gauss went offline last month so currently it is dormant in infected machines but may be activated in the future.
If the connection between Flame and Gauss turns out to be real, Gauss is another cyber espionage attempt by the American and Israeli governments although it remains to be seen why not attack Iran with Gauss like they have in the past. Maybe this was intended for Hezbollah in Lebanon and Hamas in Palestine. What a world we live in.
[via ArsTechnica, Kaspersky]

 Email article
Email article