Flame, a malware detected just recently, spreading havoc all over, currently flagged to be one of the most complex ones ever, has been targeting computers running Microsoft Windows oper ating system in the Middle East nations. CERT had announced it’s discovery on 28 May 2012, and it was categorized as ‘highly dangerous’. The code of the malware was so complex that analysts suggested it’s probability of being a state-sponsored attack (similar to Stuxnet) to be near unity.
ating system in the Middle East nations. CERT had announced it’s discovery on 28 May 2012, and it was categorized as ‘highly dangerous’. The code of the malware was so complex that analysts suggested it’s probability of being a state-sponsored attack (similar to Stuxnet) to be near unity.
Though there were only vague speculations till now about the connection between Flame and Stuxnet, recent findings by security experts at Kaspersky revealed that Flame had it’s origins in the Summer of 2008. Actually, Stuxnet, which emerged an year later had borrowed pieces of code from Flame. Discovery of many similarities in the working of both have also led to the strengthening of the visibility of the links between the two, with security experts currently speculating that both might have been developed by two independent teams, working on from late 2007.
According to Kaspersky,
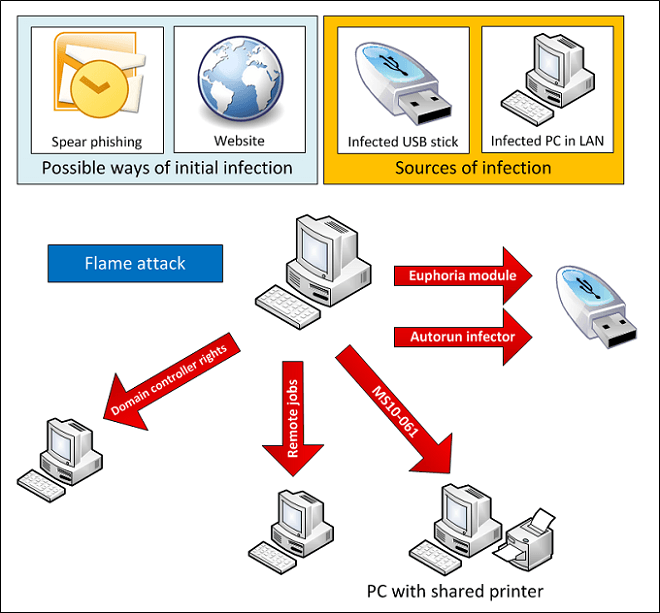
Flame can’t be cataloged as being a worm or a backdoor. Instead, it’s more like a “sophisticated attack toolkit” that is a backdoor and a Trojan with worm-like capabilities.
The amount of time put behind Flame has also amazed the analysts, with them noting the possibility of Flame being the work of a cyber-criminal organization. But security experts have not yet been able to trace the creators of the malware, though it has been named to be a ‘state-sponsored attack‘. With Flame coming out as a hot topic in the recent headlines for almost a month, the speculations on it seems to have also increased fear of the common users (probably for a good reason). But recent updates to the databases of your security software is expected to keep you safe. Many security firms have also released Flame removal tools.
But still, it is so amazing a fact that Flame has been evading all the anti-virus softwares for more than 5 years. What do you think about these recent outcries about Flame? With even the anti-virus software vendors accepting that they have not been able to detect Flame for many years, does that bother your expectation of a ‘safe tomorrow’ for your computer?
[via Softpedia | Image credit: Kaspersky]

 Email article
Email article