Update: Originally I reported that Kaspersky confirmed the hack by unu. That was a semantical mistake on my part. Kaspersky actually confirmed the vulnerability but denied a successful hack.
Update2: According to a statement by BitDefender, the BitDefender website hacked by unu is actually a website that belongs to a BitDefender partner who is authorized to sell BitDefender products to the Portuguese – it is not actually BitDefender’s website. So much better. /rolleyes
Earlier this week a hacker, that goes by the name ‘unu’, posted how he was able to hack Kaspersky’s USA website using a simple SQL injection method and gain access to what I like to call the corporate database. By now Kaspersky has confirmed that there was a vulnerability, but they deny that the hacker was successful:
Kaspersky Lab, a leading developer of secure content management systems, has detected a hacker attack on usa.kaspersky.com – the official website of the company’s US office. The attack was unsuccessful and, despite their attempts, the hackers were unable to gain access to restricted information stored on the website. Claims by the hackers responsible for the attack that they had managed to gain access to user data are untrue.
As a result of the attack, a vulnerability was found in one section of the usa.kaspersky.com website. Company personnel took immediate action to address the issue, and the vulnerability was closed a short time later.
You can make up your own mind if unu conducted a successful hack or not, but at this point I just see Kaspersky as being in denial, especially considering other people have confirmed unu’s method.
This is what Kaspersky told The Register:
“On Saturday, February 7, 2009, a vulnerability was detected on a subsection of the usa.kaspersky.com domain when a hacker attempted an attack on the site. The site was only vulnerable for a very brief period, and upon detection of the vulnerability we immediately took action to roll back the subsection of the site and the vulnerability was eliminated within 30 minutes of detection. The vulnerability wasn’t critical and no data was compromised from the site.”
Kaspersky seems to have a really broad definition of “compromised”. A third party gains access to non-public information and that is not being “compromised”? Also, apparently information like activation codes and customer email addresses are not critical. On a brighter note, the vulnerability is supposed to be fixed… just like the last 36 times they were hacked.
To add salt to the wound, The Register reports that unu tried to warn Kaspersky before publishing his findings on HackersBlog:
“I have sent emails to info@kaspersky.com, forum@kaspersky.com, and webmaster@kaspersky.com warning Kasperky [sic] about the problem but I didn’t get any response,” Unu, the hacker, said in an email. “After some time, still having no response from Kaspersky, I have published the article on hackersblog.org regarding the vulnerability.”
Anyway, as I mentioned earlier, Kaspersky can rest easy. Unu does not plan on revealing any of the information he was able to attain via his very simple, yet effective, trick.
So while the Kaspersky drama continues, unu is at it again. Only this time, the Portuguese BitDefender website is the target:
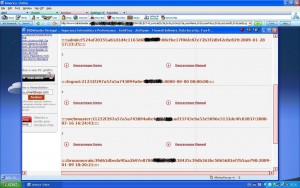
“version, user and name of the Data Base”
“Admin userName, userPass, sessionID and lastlog”
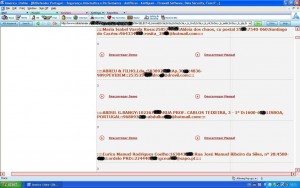
“Here’s an injection that returns thousands of lines where we see personal details of the customers, tabel vendas (sales table)”
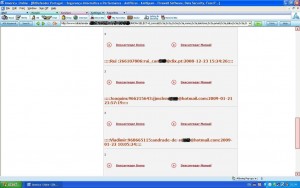
“the table inscricoes(Newsletter)… thousands of email addresses”
As with his last hack, unu originally posted this hack findings on HackersBlog.
All I have to say is that Kaspersky and BitDefender should sacrifice 10 goats to be grateful for the fact that they got lucky enough to be hacked by someone who claims to not have bad intentions (and so far he has not broken his promises).

 Email article
Email article